Attack hardware such as leave-behinds, evil maid style swaps, and supply chain compromise all introduce difficult challenges for Red Teams because the hardware does not remain in their physical control. Your Legal team is not likely to approve a scenario where keylogs could be exposed, sensitive tools could leak outside the company, or a payload risks unintentional deployment outside of scope… including a completely different company!
But it’s not just about satisfying Legal. We can also use the same solutions to test and grow the forensics capabilities of Blue Team.
In 2020, we released some features for O.MG Cable that were designed to further raise the bar on what attack hardware was capable of.
Self-Destruct allows the attacker to disarm the cable and erase sensitive data. Full functionality can only be restored once the cable is physically reclaimed and the firmware is re-flashed. Until then, the cable stays neutralized. You even have the option to disconnect the cable’s data lines to make it appear “broken”, which encourages the target to dispose of the cable.
Geofencing offers a simple, but incredibly effective way of adding autonomous functionality to the cable. You can specify a network SSID or BSSID that will trigger a payload or block the execution of a payload. This includes triggering “silent” functionality such as self-destruct.
Self-Destruct and Geofencing can be used in a variety of scenarios.
Examples:
- Behave as a normal cable until the target brings the cable into the desired office location. Once inside, execute the payload automatically. Then neutralize the cable so it once again behaves as a normal cable.
- Only allow execution if in range of your scoped target. (Prevents “I robbed the wrong bank” scenarios)
- If the cable leaves the physical scope of the engagement, trigger self-destruct to remove proprietary payload information.
- Use a hotspot on your phone to automatically trigger a payload after you have walked away from the cable. Similar to a dead man’s switch.
- Using a directional antenna to trigger payloads from a significantly extended distance. (We tested 1 mile in downtown Oakland with this method)
Forensics isn’t just for Blue Team! Red Team should know what their own tools can reveal to Blue Team. Have you checked your tools? Is your Blue Team checking?
For the O.MG Cable, you would obviously expect to find payloads and keylogs. But if you dig a bit more, you can find not only the current wifi config, but also historical networks. This means you could be exposing the credentials to a prior customer’s network, or maybe your home network that you were previously testing it on. Imagine what your other tools are leaking…
Flash.py menu for v2 firmware:
Self-destruct will remove this data. There is also a “Factory Reset” option in the latest v2 firmware flasher that can pre-emptively clear this data before you even start your exercise. But don’t take our word for it! You can use the “Backup Cable” option to create a complete forensic capture of your cable. Then open the backup image in a hex editor, or pass it through a tool like ‘strings’ to get an idea about what data is present.
Comparsions of ‘strings backup.img’ for various O.MG Cable states: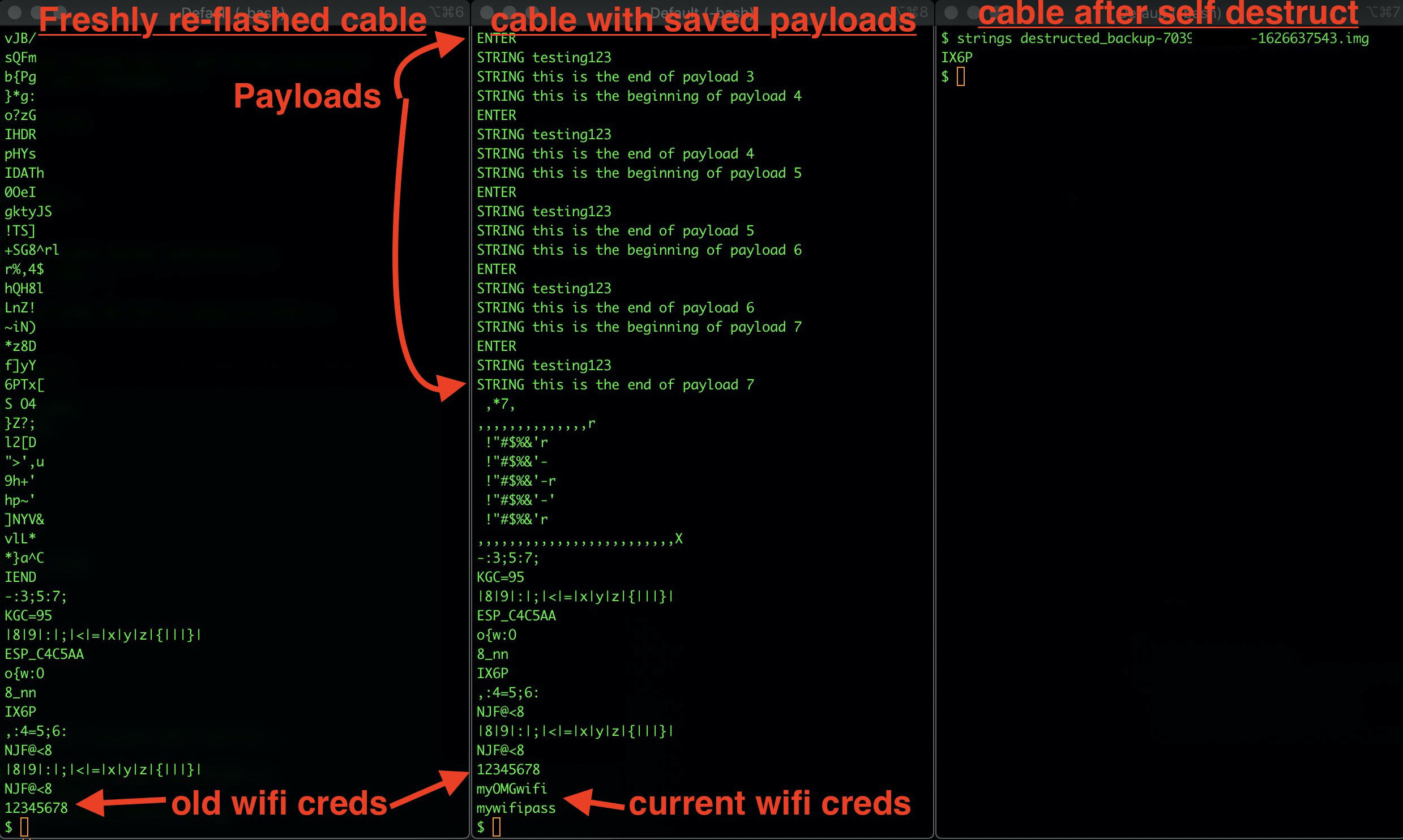
KevTheHermit did a great analysis of our v1 firmware’s self-destruct feature. He found that while self-destruct did neutralize the functionality of the O.MG Cable, there was a bug (introduced in a later version) that prevented complete erasure of sensitive data. This allowed payloads and wifi settings to be recovered. We have released a patch to address this, but this is a great example of why self-attestation is important. KevTheHermit’s automated analysis tool still works well on a cable that has not already issued a self-destruct, if the v1 firmware is used. The v2 firmware is significantly more difficult to do automated analysis against, so we suggest starting with tools like ‘strings’ and hex editors to get a wide view. (note: the v2 firmware has started introducing various types of encoding, compression, & wear leveling to optimize things. A consequence of these changes is increased difficulty in some areas of forensic analysis.)
KevTheHermit’s forensic tool for v1 firmware: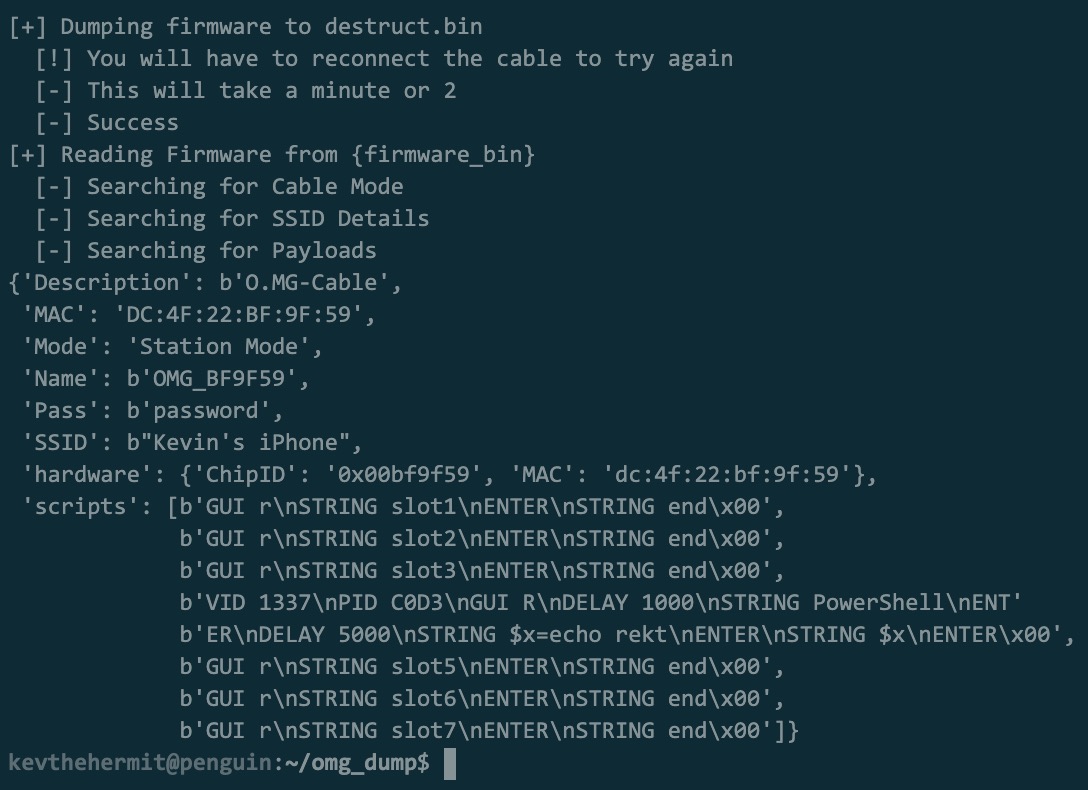
Overall, we believe it is important to think about offensive tools from many perspectives. While there is nothing wrong with making an attack demo that looks good, let’s raise the bar for what is possible.
